ViVE 2024 - Visibility Into Healthcare Data
John Emard speaks with Jason Ford from Steel Patriot Partners at ViVE 2024 about important cybersecurity topics being discussed in the Cybersecurity Pavilion.

John Emard speaks with Jason Ford from Steel Patriot Partners at ViVE 2024 about important cybersecurity topics being discussed in the Cybersecurity Pavilion.

A single view of security, application, and third-party service provider events is crucial for healthcare organizations to reduce overall business risk. It provides visibility into the environment and helps identify potential threats and attacks. Implementing technologies like Security Information and Event Management (SIEM) solutions can aid in achieving this objective. The SIEM's role expands further in the healthcare industry as it assists in meeting compliance requirements and streamlining security operations while providing a comprehensive view of security events.

Navigating the complex landscape of healthcare compliance can be daunting, even for seasoned IT professionals. The HITRUST certification, governed by the Health Information Trust Alliance, is a gold standard for ensuring compliance and the security of sensitive healthcare data. With cyber threats continually evolving, healthcare organizations face high scrutiny to safeguard patient information.
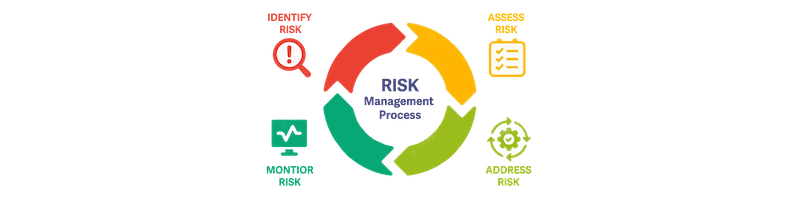
As cybersecurity challenges evolve and compliance requirements change, organizations must proactively manage the risks of protecting their sensitive information and digital assets. Risk management is a complex process that helps organizations identify compliance gaps, vulnerabilities, assess potential threats, and implement effective risk mitigation measures. The following are five best practices for risk management, specifically focusing on how it relates to cybersecurity, governance, and IT compliance.

A leading healthcare plan provider faced a common challenge: managing technical debt while ensuring robust cybersecurity measures in the public cloud. With Protected Health Information's (PHI) sensitive nature, the company needed to ensure SOC2 compliance controls were uniquely applied and refine its aging internal IT processes. Enter Steel Patriot Partners proven process.

TAMPA, FLORIDA – Schellman, a leading provider of attestation and compliance services and a top 50 CPA firm, and Steel Patriot Partners, a governance, compliance, and cybersecurity service firm, proudly announce the inclusion of Steel Patriot Partners into the Schellman Alliance Program. This inclusion joins the expertise and capabilities of two industry leaders, with the aim of delivering confident risk management and compliance.

In the rapidly evolving healthcare landscape, compliance with cybersecurity regulations is a non-negotiable requirement. Ensuring the safety of patient data and the operational continuity of your healthcare business is paramount. However, these regulations can sometimes feel cryptic. Here are six practical strategies to address compliance knowledge, risk management, and vendor management in your Healthcare organization.